The New Face ID 2 FMM 220 - 8 Possible Mishaps & the Quick Fixes
Introduction
The new Face ID 2 has recently been
updated
to
FMM 220 firmware. With it’s improved, up-to-date and much-friendlier user interface, Face ID 2 offers a few new and enhanced features that will definitely benefit its users. However, this new firmware also comes with a few errors that you might encounter and the good news is, we have a quick fix for you if you encountered these errors while running your Face ID 2.
1. AdapTec Plus is Not Working Properly
You have connected a Face ID 2 with AdapTec Plus and the AdapTec Plus is not properly working. Bear in mind that the default settings for AdapTec Plus or AdapTec X is to emit a beeping sound whenever a verification is done. However, if there is no beeps emitted from Face ID 2, you can check the settings as below:-
Menu > Comm > Wiegand Setup > Wiegand Output > ID Type = User ID (Please use “User ID” because The term “Card ID” wouldn’t work on AdapTec Plus).
Note: You need to set this settings again if you reset the device to factory settings.
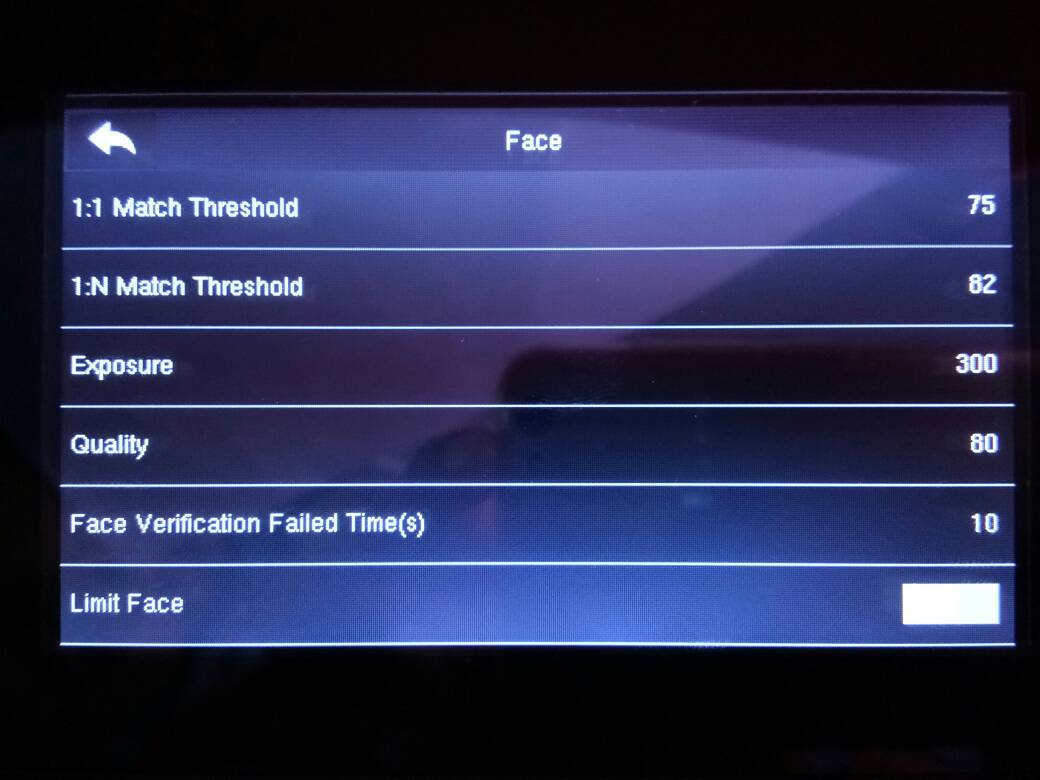
 2. The Face is Not Detected
2. The Face is Not Detected
“Limit Face” is a setting to let the machine automatically detect facial features when a user is facing Face ID. By default, the “Limit Face” will be disabled which means whenever a user is facing Face ID, the machine will detect his/her face. By enabling “Limit Face”, a user needs to select his/her clocking type such as Clock In or Clock Out before the machine will detect facial features. By using this method, the clocking type will remain the same if the next person didn’t change the clocking type when he/she clocks if the next person is using other verification method other than face (fingerprint/password). To always get the right Clocking Type, users need to select his/her own clocking type before using Face ID 2. Follow the steps below to set “Limit Face” feature:
Menu > System > Face > Limit Face = disable/enable
Note: We strongly recommend you to disable this feature to provide convenience to users.
 3. Verification Successful but the Screen is Showing Duplicate Punch
3. Verification Successful but the Screen is Showing Duplicate Punch
“Duplicate Punch” message will appear whenever a user verifies more than once after his/her initial verification. This is caused by the amount of time you set in the settings to avoid duplicate punches. You can set the amount of time in which the message will appear or just shut it off altogether.
To shut off the message, please follow the settings below :
Menu > System > Attendance > Duplicate Clocking Period (m) = None
 4. Alarm Sound Activating on Speaker
4. Alarm Sound Activating on Speaker
This alarm is triggered whenever the tamper switch at the back of device is released. This feature is important for door access use since the device is usually attached to a wall. Therefore, the alarm will go off if someone tampers or decides to remove the device. If you happen to use the device for the purpose of time attendance only, please follow the steps below to disable the speaker alarm
Note: the alarm sign will still be showing on the device
If you want to disable the alarm sound on the speaker
Menu > Access > Access Control Option > Speaker Alarm = Disable
If the Tamper Switch is released, the alarm will be muted on the speaker, but the alarm icon will still be showing on the Desktop Screen and this will in turn trigger the External Alarm.
To turn off the alarm sound when triggered, press the Tamper Switch and restart the device. Once you have done this, there will be no “Turn Off Alarm” pop up message will appear on Face ID 2 FMM.
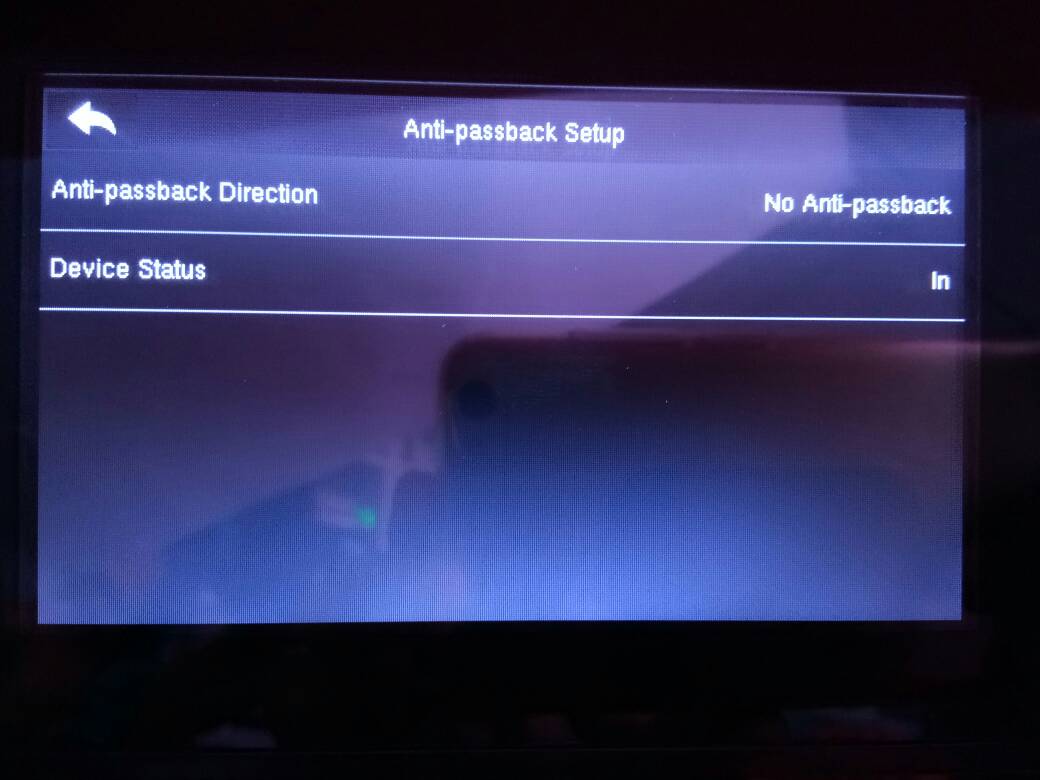
 5. Registered User is Given an “Illegal Access” Message during Verification
5. Registered User is Given an “Illegal Access” Message during Verification
This situation usually happened if the anti-passback settings are enabled.
Follow this simple step to turn off or disable the settings :-
Menu > Access > Anti-passback Setup > Anti-passback Direction = No Anti-passback
 6. Registered User is Given “Invalid Time Period” message during verification
6. Registered User is Given “Invalid Time Period” message during verification
To overcome this issue, first you need to check your device’s time zone settings and ensure that it is YOUR Time Zone. Below is how you check your Time Zone:
Menu > Access > Time Zone

If you are already within your Time Zone, please check the user's access Group settings:
You must make sure that it is configured as below :-
Menu > User Management > All User > select User ID > Edit > Access Control Role > Access Group
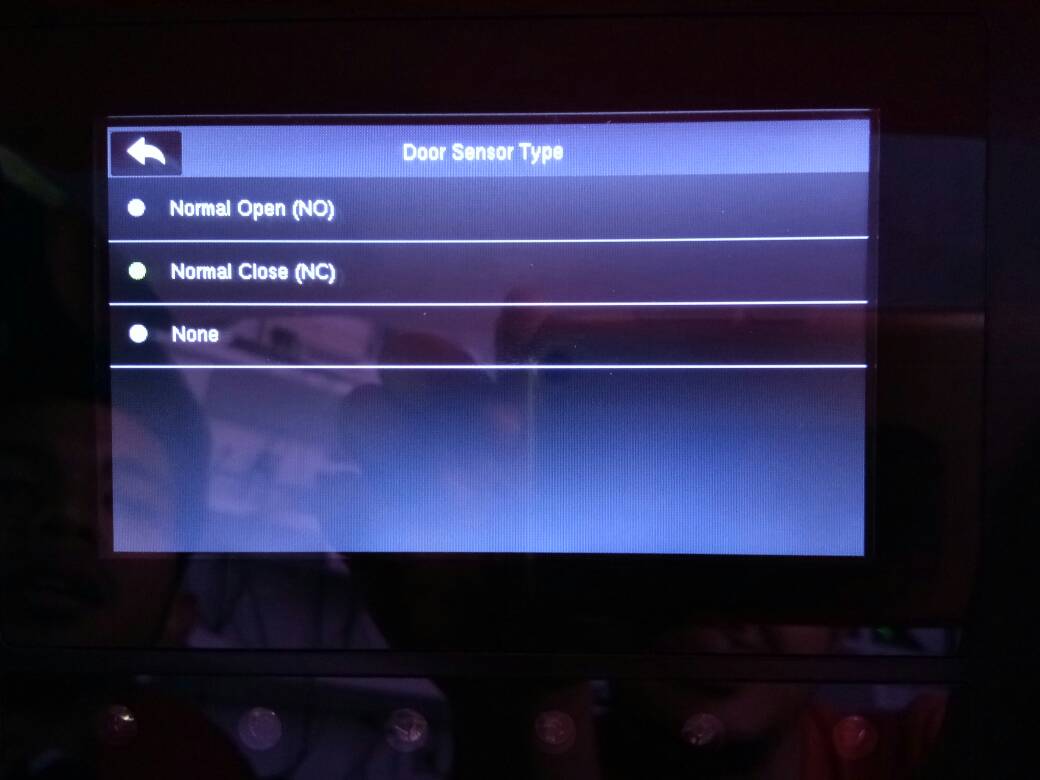
 7. Door Sensor Settings
7. Door Sensor Settings
When you are using the door access terminal, you can choose the Door Type option for the door to be used as normally open or normally close. When it is normally close, the door will be closed again after a successful access.
- Enable Door Sensor on Menu > Access > Access Control Options > Door Sensor Type = NC
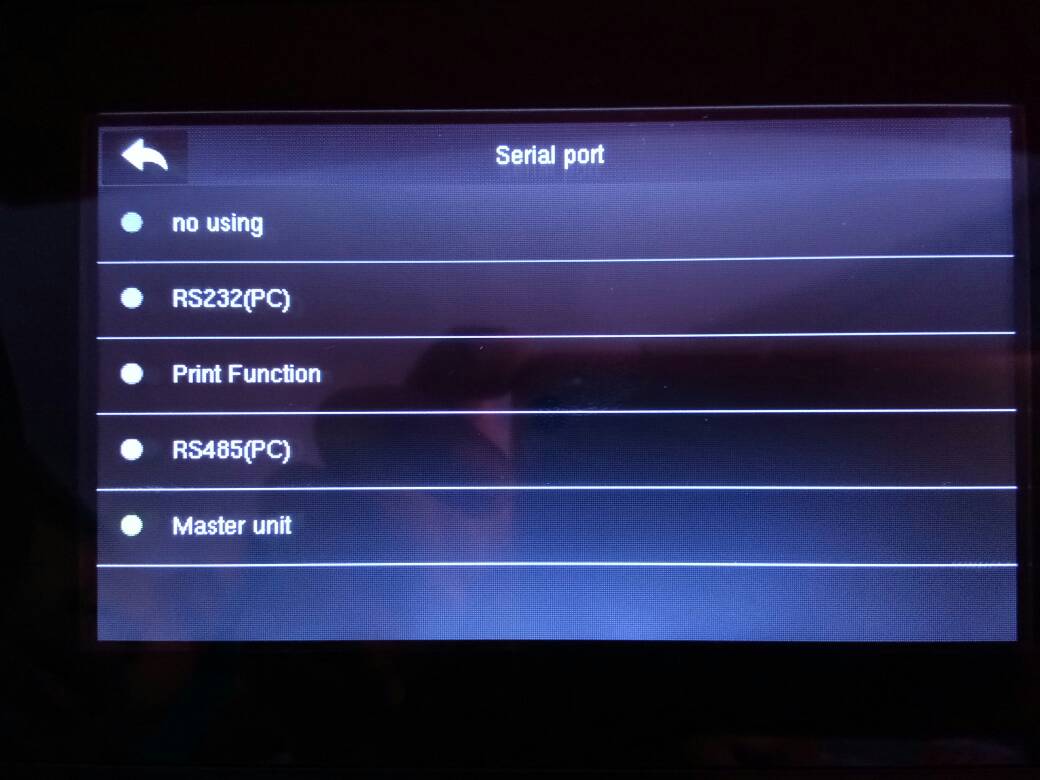
 8. Using R2c on Face ID 2 / FMM 220
8. Using R2c on Face ID 2 / FMM 220
If you want to use R2c as slave devices for Face ID 2 with FM 220; besides having a proper wiring diagram, you need to also enable the feature below :-
- Menu > Comm. > Serial Port > Master Unit/R2c






















4 comments:
Have any questions or inquiries about FingerTec? Drop your input here.